After much scrutiny and multiple privacy lawsuits, Google has initiated its plan to eliminate cookies from its web browser, Google Chrome.
The process began at the start of the New Year, with Google blocking cookies for a randomly chosen 1% of users, totaling approximately 30 million individuals. Users were given the option to enhance their browsing privacy by consenting to the blocking of third-party cookies on the platform.
This article is penned down with the aim of imparting complete information to the users on internet cookies. By exploring the functioning of cookies, its implications and its potential alternatives, the article raises an important question- how private are our lives in the digital market where we have unwittingly become the product?
Internet cookies:
Cookies are small data files that are stored in your computer each time you visit a website. Today almost every website uses cookies. Businesses utilize these cookies to assess website performance, identify popular elements, and pinpoint areas for improvement. First-party cookies, provided directly by website owners, are generally considered safer as their purpose is explicitly stated. These cookies also enable website owners to understand their customers' online behavior, particularly on their own site.
For the customers, cookies add a touch of personalization by remembering user preferences such as shopping items, read content and themes. This increases customer satisfaction.
However, the majority of websites rely on a different type of cookies – third-party cookies. These cookies are provided by external entities like Google Analytics, Meta, or Twitter. These cookies come into play when websites incorporate third-party services such as share buttons or YouTube videos into their websites.
Understanding the working of third-party cookies:
When you visit a website, your browser seeks permission from the host website and all associated third parties to open the webpage. To facilitate this, both the third party and the host store small data packets, or cookies, in your browser. These cookies contain information necessary for accessing third-party services. For example, to open a YouTube video, a JavaScript would be needed, or a share button on the website would need to keep track of the number of shares; this information would be stored in the form of cookies in your web browser to enhance the overall web experience.
On paper, there seems to be no issue, as these cookies contribute to seamless video loading and a smooth website experience. The problem arises when third-party services provide these cookies. These cookies are placed on your device by websites different from the one you're currently visiting. For example, if a news website embeds a YouTube video, YouTube can insert a cookie on your device. This gives You Tube the access to monitor your activity across other websites utilizing YouTube videos.
Third-party cookies are provided by third-party service providers as a tool to deliver their services, track user behavior, and ultimately generate revenue. Notable companies in this realm are Google, Facebook, Adobe and Twitter.
Recognizing the risks of third-party cookies:
Third-party cookies are provided by third-party service providers. We are not directly linked to these services, yet they can track our data through cookies. In the mentioned example, a news website utilizing a YouTube video allows YouTube to implant a cookie in your web browser. Subsequently, when you visit other websites embedding YouTube links, YouTube employs the same cookie to monitor all your website visits.
Although the gravity of this concern may not be immediately apparent in the given example; consider this perspective: nearly every modern website features a share button, granting direct access to share button providers, typically Meta (which owns Facebook, WhatsApp, Instagram) and Google. This access enables them to track your activity across multiple platforms.
However, this only scratches the surface of the issue. Our data, until now, has been accumulated and stored by third-party service providers, even though we didn't initially share this data with them.
While it may be tempting to assume that our credentials are secure in their hands, there is some validity to this assumption. Notably, companies such as Google and Meta adhere to stringent international laws like the General Data Protection Regulation (GDPR) and privacy guidelines outlined by the Organization for Economic Co-operation and Development (OECD). These regulations act as a safeguard which limit companies from indiscriminately sharing our data with external entities.
But there is a catch. Our digital data is not stored in one huge set; it is rather meticulously categorized in five different subsets, all of which have different characteristics and importance among analysts, researchers and marketers.
Categorization of digital data:
All of our digital activities, also called our digital footprint, are stored in the form of data, which invariably connects to our real-world identities.
- The direct identifying data: This encompasses our name, phone numbers, passwords, and bank details. This data is unique to individuals and directly links to them. It holds paramount importance for marketing strategies, analysis, and market surveys. This facilitates in purposeful ad generation for the user- which user is most likely to respond and interact with.
- Indirect Identifiers: Information like location, address, and date of birth falls into this category. While lacking direct identifiers such as names and numbers, this data holds crucial details about users. Tracing individuals becomes somewhat challenging, though not impossible. With a bit of data engineering, the real identity of the person can be unveiled.
- Communal Data: This type involves information linked to multiple individuals, like movie preferences among customers. It provides insights into collective trends or behaviors shared among groups of people.
- Generalized data: The data that is gathered from surveys and location tracking, which does not link to a specific person, but a group of people is called generalized data.
- Non-individual data: This data is detached from personal identities such as earthquake patterns or weather reports.
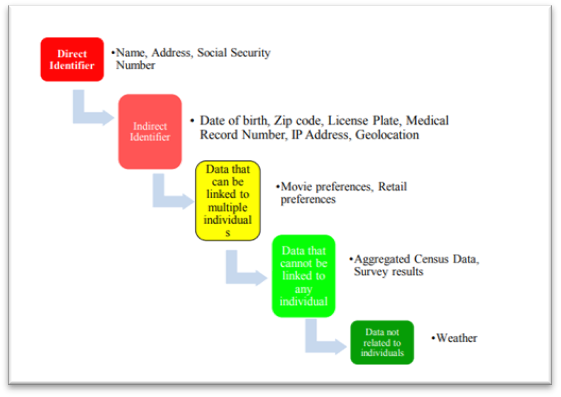 |
Fig: Categorization of digital data
This data set serves as the foundation for research projects, surveys, market research, and critical innovations. However, it cannot be shared with customers in its original form. So, companies adapt to the practice of data anonymity.
The curious case of data anonymity:
The intriguing aspect of data anonymity comes to light when considering that companies like Google cannot directly share our details. Instead, they resort to distorting the data.
For example, a medical company aiming to track and find cures for diseases requires access to patients' medical histories. While sharing the names of patients is avoided to uphold privacy, sharing their medical history becomes essential. In such cases, computer programs are employed to alter names, numbers, and other direct or indirect identifiers of the patients, while keeping the medical history intact. This type of data is called anonymous data.
This anonymization process involves replacing names with generic labels like "Name 1" and "Name 2," or generalizing ages from a specific range, such as 65 years to 60-70 years. To maintain data relevance, numerical values may be adjusted by adding or subtracting consistent amounts. In some instances, a layer of noise is introduced, similar to blurring a person's face in images for data privacy. Subsequently, after this data alteration, it becomes available for sharing without compromising individual identities.
However, mere data alteration is not enough to guarantee complete digital privacy. Little reverse engineering on the data can still lead to us.
Re-identification of the data:
Reidentifying the data is challenging but is possible, as people have demonstrated in the past. In 2007, researchers released a study attempting to de-anonymize Netflix's movie rating data, even though it supposedly excluded usernames and IDs. By combining these ratings with publicly available information like movie release dates and IMDB listings, researchers were able to successfully identify some users with 85% accuracy. This case demonstrates the vulnerability of even seemingly anonymized data to re-identification, especially when combined with other sources of information.
In 2018, a report showed how Strava, a fitness app, inadvertently leaked the locations of military personnel stationed overseas through its heat map feature, which aggregated anonymized user activity data. This incident demonstrates how location data, even when anonymized, can be used to infer sensitive information about individuals and potentially endanger them.
Another issue with the third party cookies is also that it gathers data without user’s consent, resulting in the loss of privacy and trust of the user.
Addressing these issues, companies have introduced added security patterns and frequently changing computer algorithms to toughen data hacking, but why not nip the evil in the bud!
That is why the government has emphasized on blocking third-party cookies on the internet. Google is actively contributing to this cause by eliminating third-party cookies and introducing the Privacy Sandbox initiative. The new initiative by Google aims to develop a set of open standards and rules to replace cookies.
This would support digital advertising on the web without compromising their privacy. It aims to create an environment where cookies would no longer be required for targeted ads; rather it would be done through sophisticated APIs and computer programs which will enhance user privacy.
Although Google claims that this would also provide better opportunities to advertisers, analysts believe that this would increase monopoly in the market. The same is under observation by UK’s digital competition monitoring body- Digital Markets Unit (DMU).
Other potential consequences of blocking third-party cookies for businesses include a lack of insight into customer behavior and preferences, as well as a potential decrease in personalized experiences for customers. Without third-party cookies, businesses may have a harder time understanding which areas of their website need improvement and may not be able to provide as tailored of an experience for their customers. However, the impact of blocking third-party cookies is still being studied and the full extent of its effects remains to be seen.
Conclusion:
In conclusion, digital data privacy stands as a significant concern for policymakers. Although efforts are underway to establish laws and regulations, it is essential to reflect on how effortlessly data can be accessed online, with all our information just a few clicks away.
Copyright © 2026 getessayservice.com

